Serverless computing using the IBM Cloud as an example
The IT sector "Cloud" is constantly growing and offers customers various services and thus a diverse range of possibilities. In the blog post "What is serverless computing?" we described the concepts of serverless computing and possibilities, as well as advantages and disadvantages of using these services. We also went into more detail on the topic of AWS Lambda. The following article looks at how serverless computing works in the IBM Cloud environment.
What serverless computing capabilities does the IBM Cloud offer?
The IBM Cloud offers a Function-as-a-Service (FaaS) solution called IBM Cloud™ Functions. This allows you to execute application logic in response to events or direct calls to web or mobile applications over HTTP, all without the use of server infrastructure. Cloud Functions takes care of system management, such as availability management and maintenance, so you, the developer, can focus on writing application logic. (Source)
How to start with IBM Cloud functions
Development can start from two ways:
1. Cloud Functions UI
2. Cloud Functions command-lineinterface (CLI), which provides more control over your deployment and operations
Both ways producethe same results. The procedural steps are similar for both paths and arelisted below as a step-by-step guide. (Source)
- Step 1: Creating an IBM Cloud account and log in
- Step 2: Navigate to Cloud Functions dashboard
- Step 3: Select a namespace (required)
- Step 4: Click Start Creating > Quickstart Templates and select the HelloWorld template
- Step 5: Create a package for your action by entering a unique name in the Package Name field
- Step 6: Select a runtime for your action. You can preview the code for the sample action in each available runtime before you deploy the template
- Step 7: Click Deploy. You created an action. Great job!
- Step 8: Run the action by clicking Invoke. Invoking an action manually runs the app logic that the action defines. In the Activations panel, you can see the "Hello stranger!" greeting produced by the action
- Step 9: Optional: Click Change Input to change the action or try your own
- Step 10: THAT’S ALL! To clean up this action, click the overflow menu and select Delete Action
This is how IBM Cloud™ Functions works from a technical perspective
Cloud Functions is based on OpenWhisk, an open source project that combines components such as NGINX, Kafka, Docker, and CouchDB to form a serverless event-based programming service. (Source)
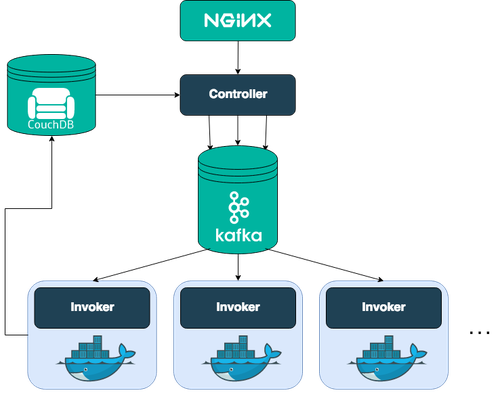
The first entry point into the system is through NGINX, an HTTP and reverse proxy server. NGINX is used for SSL termination and forwarding appropriate HTTP calls. NGINX forwards the HTTP request to the Controller, the next component on the path throughOpenWhisk. The controller is a Scala-based implementation of the actual RESTAPI (based on Akka and Spray). As such, the controller serves as the interface for everything that you want to do, including create, retrieve, update, and delete requests for your entities in OpenWhisk and the invocation of actions. Now the controller verifies who you are (Authentication) and whether you have the required privileges to do what you want to do with thatentity (Authorization). The credentials that are included in the request are verified against the so-called subjects database in a CouchDB instance. After the controller determines that you are authenticated and authorized to invokethe action, it loads the action from the whisks database in CouchDB. The Load Balancer, knowing which Invokers are available, chooses one of them to invokethe action that you requested. The controller and the Invoker solely communicate through messages that are buffered and persisted by Kafka.Kafka lifts the burden of buffering in memory from both the controller and the Invoker, while also making sure that messages are not lost if a system crashes. To run actions in an isolated and safe way, Docker is used to set up a self-encapsulated environment (called a container) for each action that is invoked. After the container is created, the code is injected and then run with the parameters that were passed to it. When the results are returned, the container is destroyed. Performance optimizations can be done at this stage to reduce maintenance requirements and make low response times possible. After the result is obtained by the Invoker, it is stored into the whisks database as an activation under the assigned activation ID. The whisks database lives in CouchDB.
Pros and Cons of IBM serverless functions
In general, IBM Cloud™ Functions are useful for smaller tasks in mobile applications with non-continuous calls. Advantages here are scalability, easy triggering and file validation. IBM Cloud™ Functions are suitable for companies with compact processes, among others. (Source)
The Libelle IT Group also relies on the advantages of the cloud and provides you with various solutions. Use the cloud editions of Libelle DataMasking (AWS / Microsoft Azure), Libelle SystemCopy (AWS / Microsoft Azure) or Libelle CloudShadow (IBM Cloud) now.
Recommended article
All blog articles